JSON Web Tokens (JWTs) are an open standard used in the realm of web security, enabling secure data transmission between two parties. At their core, JWTs are compact, self-contained tokens designed for secure communication. They consist of three parts: a header, a payload, and a signature. This structure allows them to carry information about the user, ensuring that data exchanges are both safe and reliable. For developers and security enthusiasts alike, understanding JWTs is crucial for building and maintaining secure web applications. Whether you're authenticating user sessions or securing RESTful APIs, JWTs play a pivotal role in web security. In this introduction, we'll unveil 20 fascinating facts about JWTs, shedding light on their functionality, versatility, and why they've become a staple in web security protocols.
Understanding JWTs
JSON Web Tokens (JWTs) are an open standard for securely transmitting information between parties as a JSON object. This information can be verified and trusted because it is digitally signed. JWTs can be signed using a secret (with the HMAC algorithm) or a public/private key pair using RSA or ECDSA.
-
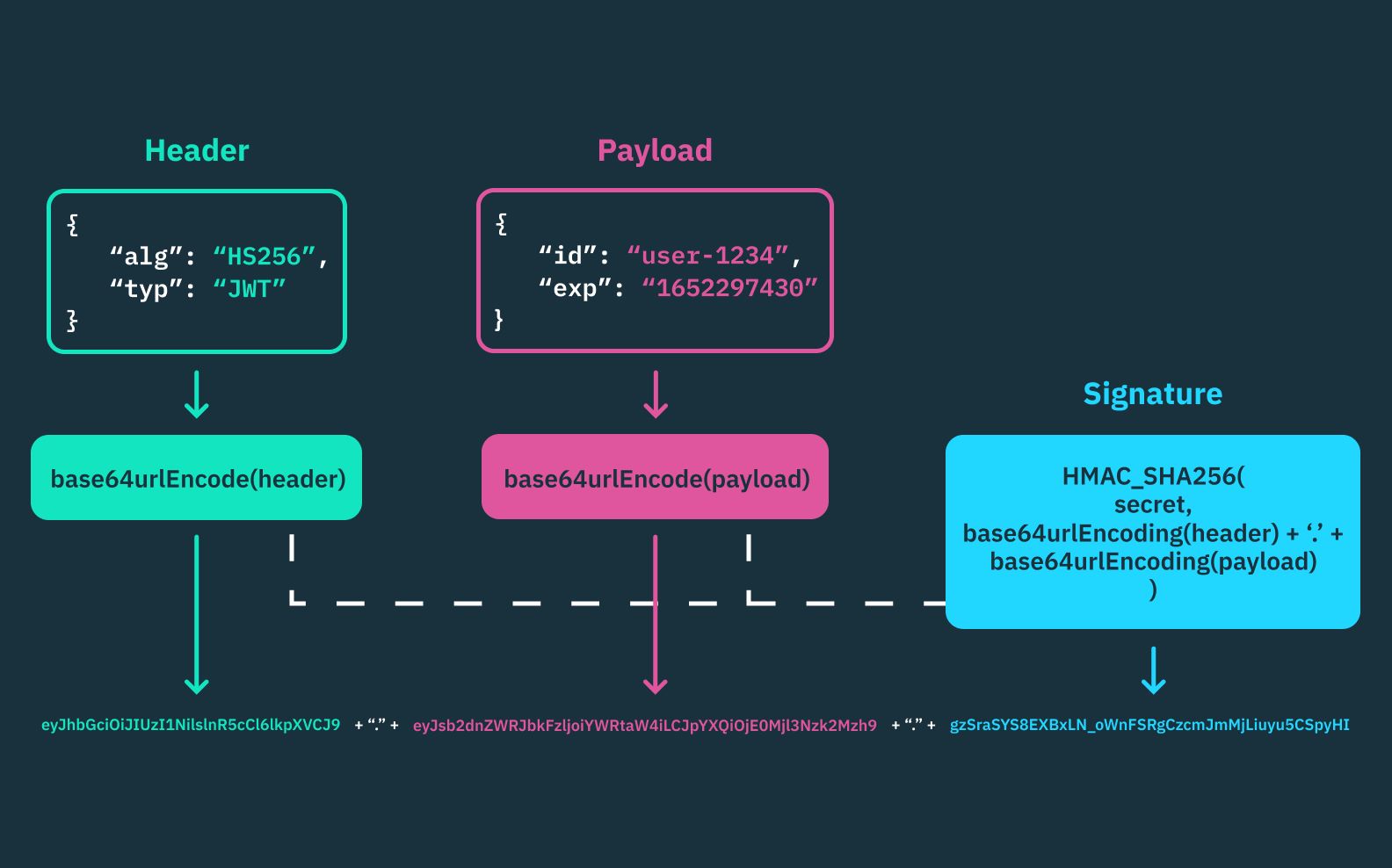
JWTs consist of three parts: Header, Payload, and Signature. These parts are separated by dots (.) and are typically represented as a compact, URL-safe string.
-
The Header typically consists of two parts: the type of token, which is JWT, and the signing algorithm being used, such as HMAC SHA256 or RSA.
-
Payload contains the claims. Claims are statements about an entity (typically, the user) and additional data. There are three types of claims: registered, public, and private claims.
-
Signature is used to secure the token and verify that the sender of the JWT is who it says it is and to ensure that the message wasn't changed along the way.
How JWTs Work
-
To create a JWT, you must encode the header, payload, and signature, then concatenate them with dots. When the token is used in a request, the server decodes it and verifies the signature to ensure its integrity.
-
JWTs are stateless. They contain all the necessary information about the user, eliminating the need to store session information on the server. This makes JWT a good choice for scalability.
Uses of JWTs
-
JWTs are commonly used for authorization. Once the user is logged in, each subsequent request will include the JWT, allowing the user to access routes, services, and resources that are permitted with that token.
-
They are also used in information exchange. Because JWTs can be signed—for example, using public/private key pairs—you can be sure the senders are who they say they are and the contents haven't been tampered with.
Advantages of JWTs
-
Compactness: JWTs can be sent through a URL, POST parameter, or inside an HTTP header. Their small size makes them easy to transmit.
-
Security: With proper implementation and when using a strong signing algorithm, JWTs offer a secure way to handle authentication and authorization.
-
Flexibility: JWTs can be used across multiple domains, making them ideal for single sign-on (SSO) scenarios.
Common Misconceptions about JWTs
-
Not a silver bullet for security: While JWTs are secure, they must be implemented correctly. Poor practices, like not validating the token properly, can lead to security vulnerabilities.
-
Storage: Storing JWTs in local storage is convenient but can make them susceptible to cross-site scripting (XSS) attacks. Secure storage options should be considered.
Best Practices for Using JWTs
-
Keep it short-lived: To mitigate the risk of token theft, JWTs should have a short expiration time.
-
Use HTTPS: To prevent man-in-the-middle attacks, always transmit JWTs over HTTPS.
-
Validate the token: Always validate the JWT on the server side to ensure it's valid and hasn't been tampered with.
JWTs and Modern Web Applications
-
Single Page Applications (SPAs) often use JWTs for maintaining user sessions and for communicating with backend services securely.
-
Microservices architectures benefit from JWTs as they provide a lightweight and stateless way to secure communications between services.
Future of JWTs
-
With the rise of distributed systems and the need for efficient, secure ways to manage authentication and authorization, JWTs are likely to remain a key component in web security.
-
Innovations in cryptography and security practices will continue to evolve JWTs, making them even more secure and efficient for web applications.
Piecing Together the JWT Puzzle
JWTs, or JSON Web Tokens, stand as a cornerstone in modern web security, offering a compact and self-contained way for securely transmitting information between parties. Understanding these tokens is crucial for developers and security professionals alike, as they play a pivotal role in authentication and information exchange processes. With their ability to be quickly verified and trusted due to their digital signature, JWTs streamline the authentication process, making web applications more efficient and user-friendly. Remember, while JWTs offer numerous benefits, including scalability and flexibility, they must be implemented with caution to avoid common security pitfalls. Armed with the knowledge of how JWTs work and their potential vulnerabilities, you're now better equipped to harness their power responsibly in your projects. Keep exploring, keep learning, and let JWTs enhance your web security measures.
Was this page helpful?
Our commitment to delivering trustworthy and engaging content is at the heart of what we do. Each fact on our site is contributed by real users like you, bringing a wealth of diverse insights and information. To ensure the highest standards of accuracy and reliability, our dedicated editors meticulously review each submission. This process guarantees that the facts we share are not only fascinating but also credible. Trust in our commitment to quality and authenticity as you explore and learn with us.


