LDAP servers are crucial for managing and accessing directory information in networks. But what exactly is an LDAP server? LDAP stands for Lightweight Directory Access Protocol, a protocol used to access and manage directory services over a network. These servers store data in a hierarchical structure, making it easier to organize and retrieve information. They are widely used in various applications, from email systems to network management. Understanding LDAP servers can help you streamline authentication processes, enhance security, and improve overall network efficiency. Ready to dive into the world of LDAP servers? Here are 40 facts to get you started!
What is LDAP?
LDAP stands for Lightweight Directory Access Protocol. It's a protocol used to access and manage directory information over an IP network. Here are some interesting facts about LDAP servers.
-
LDAP was developed in the early 1990s as a simpler alternative to the Directory Access Protocol (DAP) used by X.500 directories.
-
LDAP is widely used in various applications, including email systems, network operating systems, and enterprise resource planning (ERP) systems.
-
LDAP directories store information in a hierarchical structure, similar to a tree, with entries organized in branches and leaves.
-
Each entry in an LDAP directory is identified by a unique Distinguished Name (DN), which includes the entry's location in the directory hierarchy.
-
LDAP supports both read and write operations, allowing users to search for, retrieve, and modify directory information.
How LDAP Works
Understanding how LDAP functions can help you appreciate its utility in managing directory services.
-
LDAP uses a client-server model, where clients send requests to LDAP servers, which process the requests and return responses.
-
LDAP servers typically listen on port 389 for unencrypted communication and port 636 for encrypted communication using SSL/TLS.
-
LDAP operations are performed using a set of defined protocols, including bind, search, compare, add, delete, modify, and unbind.
-
The bind operation establishes a connection between the client and the server, often requiring authentication.
-
The search operation allows clients to query the directory for specific information based on various criteria.
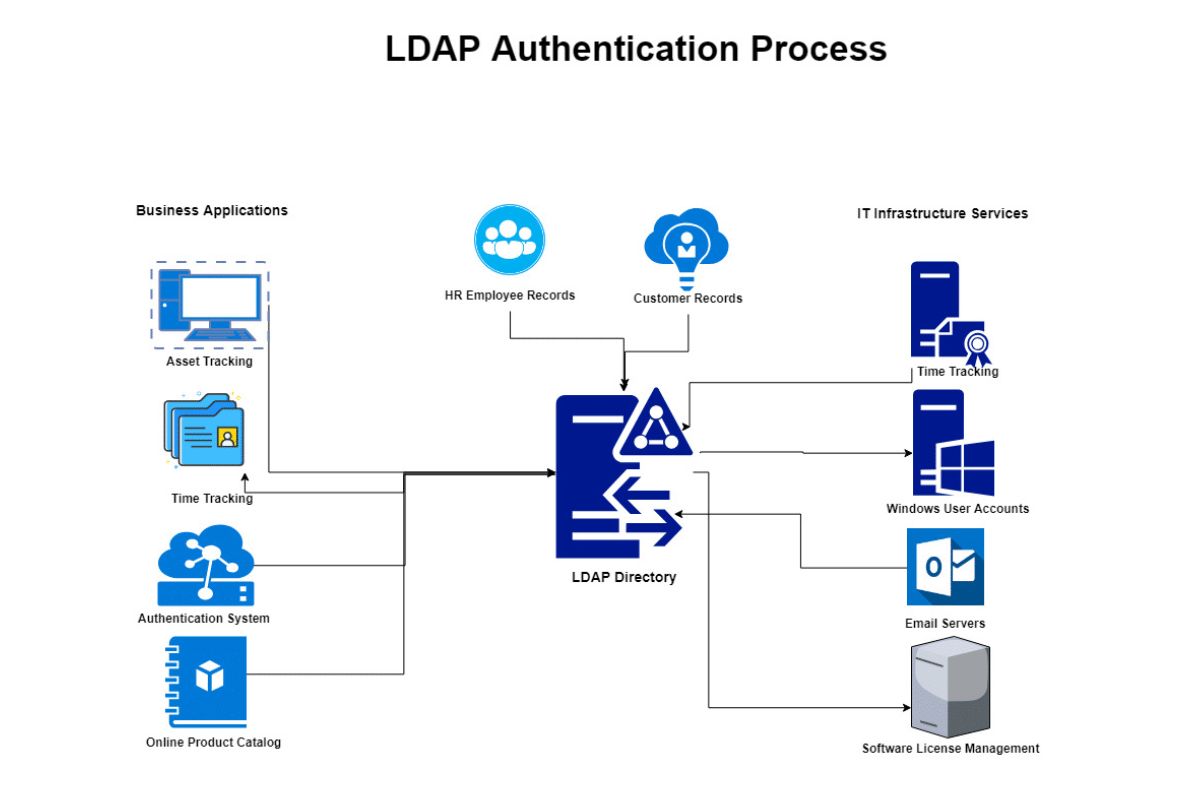
LDAP Authentication
LDAP is often used for authentication purposes, providing a centralized way to manage user credentials.
-
LDAP supports various authentication methods, including anonymous, simple, and SASL (Simple Authentication and Security Layer).
-
Simple authentication involves sending a username and password to the server, while SASL provides more secure mechanisms like Kerberos and DIGEST-MD5.
-
LDAP can be integrated with other authentication systems, such as Active Directory, to provide single sign-on (SSO) capabilities.
-
LDAP authentication can be used to control access to network resources, applications, and services.
-
Many organizations use LDAP to manage user accounts, passwords, and permissions across multiple systems.
LDAP Schema
The schema defines the structure of the directory, specifying the types of entries and attributes that can be stored.
-
An LDAP schema consists of object classes and attribute types, which define the rules for directory entries.
-
Object classes represent different types of directory entries, such as users, groups, and devices.
-
Attribute types define the specific pieces of information that can be associated with an entry, such as names, email addresses, and phone numbers.
-
LDAP schemas can be extended to include custom object classes and attribute types, allowing organizations to tailor the directory to their needs.
-
Schema definitions are typically stored in a special part of the directory called the schema subentry.
LDAP Security
Security is a critical aspect of LDAP, ensuring that directory information is protected from unauthorized access and tampering.
-
LDAP supports SSL/TLS encryption to secure communication between clients and servers.
-
Access control lists (ACLs) can be used to define who can access or modify specific parts of the directory.
-
LDAP servers can enforce password policies, such as minimum length, complexity, and expiration, to enhance security.
-
Many LDAP implementations support replication, allowing directory data to be copied to multiple servers for redundancy and load balancing.
-
LDAP logs can be used to monitor and audit directory activity, helping to detect and respond to security incidents.
LDAP Implementations
There are several popular LDAP implementations, each with its own features and capabilities.
-
OpenLDAP is an open-source implementation of LDAP, widely used in various environments.
-
Microsoft Active Directory is a proprietary LDAP implementation that provides additional features like Group Policy and integration with Windows domains.
-
Apache Directory Server is another open-source LDAP implementation, designed to be extensible and embeddable.
-
389 Directory Server, formerly known as Fedora Directory Server, is an open-source LDAP server developed by Red Hat.
-
Oracle Directory Server Enterprise Edition is a commercial LDAP implementation with advanced features like multi-master replication and high availability.
LDAP Use Cases
LDAP is used in a variety of scenarios, providing a flexible and scalable solution for directory services.
-
LDAP is commonly used for user authentication and authorization in web applications and services.
-
Many email systems use LDAP to store and retrieve user information, such as email addresses and distribution lists.
-
LDAP directories can be used to manage network resources, such as printers, file shares, and network devices.
-
Organizations often use LDAP to store and manage contact information for employees, customers, and partners.
-
LDAP can be integrated with other directory services, such as NIS and DNS, to provide a unified directory infrastructure.
LDAP Challenges
Despite its many benefits, LDAP also presents some challenges that organizations need to address.
-
LDAP can be complex to set up and configure, requiring a good understanding of directory services and protocols.
-
Ensuring the security of LDAP directories can be challenging, particularly in large and distributed environments.
-
LDAP performance can be affected by factors such as directory size, network latency, and server load.
-
Schema design and management can be complex, particularly when extending the schema to include custom object classes and attributes.
-
Integrating LDAP with other systems and applications can be challenging, particularly when dealing with proprietary or legacy systems.
Final Thoughts on LDAP Servers
LDAP servers play a crucial role in managing and accessing directory information. They streamline user authentication, making it easier for organizations to maintain secure and efficient systems. With LDAP, you get centralized control over user data, which simplifies administrative tasks and enhances security.
Understanding LDAP's structure and functionality can significantly benefit IT professionals and organizations. From improving access control to enabling seamless integration with various applications, LDAP servers offer numerous advantages.
Whether you're setting up a new system or optimizing an existing one, knowing these 40 facts about LDAP servers can help you make informed decisions. Keep these insights in mind to leverage LDAP's full potential, ensuring your directory services are robust and reliable.
Thanks for sticking around and diving into the world of LDAP servers. Happy managing!
Was this page helpful?
Our commitment to delivering trustworthy and engaging content is at the heart of what we do. Each fact on our site is contributed by real users like you, bringing a wealth of diverse insights and information. To ensure the highest standards of accuracy and reliability, our dedicated editors meticulously review each submission. This process guarantees that the facts we share are not only fascinating but also credible. Trust in our commitment to quality and authenticity as you explore and learn with us.
