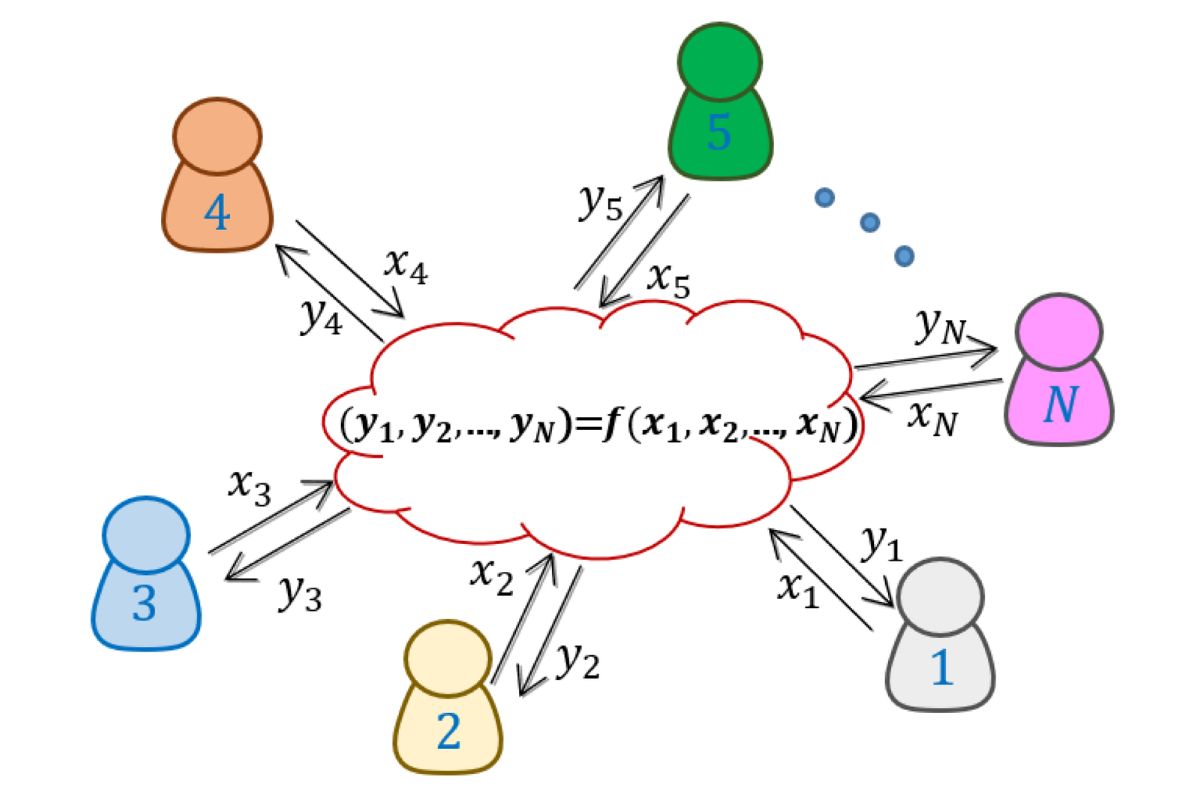
What is Secure Multi-party Computation (SMPC)? Secure Multi-party Computation (SMPC) is a cryptographic method that allows multiple parties to jointly compute a function over their inputs while keeping those inputs private. Imagine you and your friends want to find out who has the highest salary without revealing your actual salaries. SMPC makes this possible. It ensures data privacy and security, even if some participants are untrustworthy. This technology is crucial in fields like finance, healthcare, and voting systems, where sensitive information must remain confidential. By using SMPC, organizations can collaborate without compromising individual privacy, making it a powerful tool in today's data-driven world.
What is Secure Multi-party Computation?
Secure Multi-party Computation (SMPC) is a cryptographic protocol that allows multiple parties to jointly compute a function over their inputs while keeping those inputs private. This technology is crucial for privacy-preserving applications in various fields. Let's dive into some fascinating facts about SMPC.
-
Origins in the 1980s
SMPC was first introduced in the 1980s by Andrew Yao, a computer scientist. He proposed the concept of "Yao's Millionaires' Problem," where two millionaires want to know who is richer without revealing their actual wealth. -
Cryptographic Foundations
SMPC relies on cryptographic techniques like secret sharing, homomorphic encryption, and zero-knowledge proofs to ensure data privacy and security. -
Applications in Voting Systems
One of the earliest applications of SMPC was in secure electronic voting systems, where it ensures that votes remain confidential while still being counted accurately. -
Healthcare Data Sharing
SMPC enables secure sharing of sensitive healthcare data among institutions for research purposes without compromising patient privacy. -
Financial Services
Financial institutions use SMPC to perform joint risk assessments and fraud detection without exposing sensitive customer data. -
Collaborative Machine Learning
SMPC allows multiple organizations to collaboratively train machine learning models on their combined data sets without sharing the actual data. -
Blockchain Integration
SMPC can be integrated with blockchain technology to enhance privacy and security in decentralized applications. -
Privacy-Preserving Advertising
Advertisers use SMPC to target ads more effectively without accessing users' personal information directly. -
Government and Defense
Governments and defense organizations use SMPC to share intelligence and perform joint operations securely. -
Supply Chain Management
SMPC helps companies in a supply chain collaborate on logistics and inventory management without revealing proprietary information.
How Does Secure Multi-party Computation Work?
Understanding the mechanics of SMPC can be complex, but here are some simplified facts to help grasp the concept.
-
Secret Sharing
In SMPC, data is divided into multiple shares, and each party receives a share. No single party can reconstruct the original data without combining all the shares. -
Homomorphic Encryption
This technique allows computations to be performed on encrypted data without decrypting it, ensuring data privacy throughout the process. -
Zero-Knowledge Proofs
Zero-knowledge proofs enable one party to prove to another that a statement is true without revealing any additional information. -
Garbled Circuits
Garbled circuits are used in SMPC to securely evaluate boolean circuits, ensuring that inputs remain private. -
Oblivious Transfer
Oblivious transfer is a cryptographic protocol used in SMPC to transfer data between parties without revealing which data was transferred. -
Threshold Cryptography
In threshold cryptography, a certain number of parties must collaborate to perform a cryptographic operation, enhancing security. -
Multiplicative and Additive Secret Sharing
These techniques allow parties to perform arithmetic operations on shared data without revealing the data itself. -
Secure Function Evaluation
SMPC protocols enable parties to jointly evaluate a function on their inputs while keeping those inputs private. -
Communication Complexity
SMPC protocols often require significant communication between parties, which can be a challenge in practical implementations. -
Computational Overhead
The cryptographic operations in SMPC can introduce computational overhead, making it slower than traditional computation methods.
Real-World Implementations of SMPC
SMPC is not just theoretical; it has real-world applications that impact various industries.
-
Google's RAPPOR
Google uses SMPC in its RAPPOR system to collect user data while preserving privacy. -
Facebook's Private Lift Measurement
Facebook employs SMPC to measure the effectiveness of advertising campaigns without accessing individual user data. -
IBM's Secure Collaborative Analytics
IBM has developed SMPC-based solutions for secure collaborative analytics in industries like healthcare and finance. -
Microsoft's SEAL
Microsoft SEAL is an open-source library that provides tools for implementing SMPC and homomorphic encryption. -
DARPA's Brandeis Program
The Defense Advanced Research Projects Agency (DARPA) has funded research into SMPC to enhance data privacy and security. -
Alibaba's Privacy-Preserving Computation
Alibaba uses SMPC to enable secure data collaboration between different business units and partners. -
Intel's SGX
Intel's Software Guard Extensions (SGX) provide hardware-based support for SMPC, enhancing security and performance. -
Enigma Protocol
The Enigma protocol uses SMPC to enable decentralized applications with strong privacy guarantees. -
Partisia Blockchain
Partisia Blockchain integrates SMPC to provide privacy-preserving smart contracts and decentralized applications. -
Ocean Protocol
Ocean Protocol uses SMPC to enable secure data sharing and monetization in a decentralized data marketplace.
Challenges and Future of SMPC
Despite its potential, SMPC faces several challenges that need to be addressed for broader adoption.
-
Scalability Issues
SMPC protocols can be resource-intensive, making them difficult to scale for large datasets and complex computations. -
Usability Concerns
Implementing SMPC requires specialized knowledge in cryptography, which can be a barrier for widespread adoption. -
Regulatory Compliance
Ensuring that SMPC implementations comply with data protection regulations like GDPR and CCPA is crucial for their success.
The Power of Secure Multi-party Computation
Secure Multi-party Computation (SMPC) is a game-changer. It allows multiple parties to collaborate on computations without revealing their private data. This tech is crucial for industries like finance, healthcare, and cybersecurity. It ensures data privacy while enabling complex calculations. SMPC can prevent data breaches and protect sensitive information. It’s not just about security; it’s about trust and collaboration. As more organizations adopt SMPC, we’ll see a shift towards more secure and efficient data handling. This tech isn’t just for experts; it’s becoming more accessible. Understanding SMPC can give you a competitive edge in today’s data-driven world. So, whether you’re a tech enthusiast or a business leader, keep an eye on SMPC. It’s paving the way for a safer, more collaborative future.
Was this page helpful?
Our commitment to delivering trustworthy and engaging content is at the heart of what we do. Each fact on our site is contributed by real users like you, bringing a wealth of diverse insights and information. To ensure the highest standards of accuracy and reliability, our dedicated editors meticulously review each submission. This process guarantees that the facts we share are not only fascinating but also credible. Trust in our commitment to quality and authenticity as you explore and learn with us.
