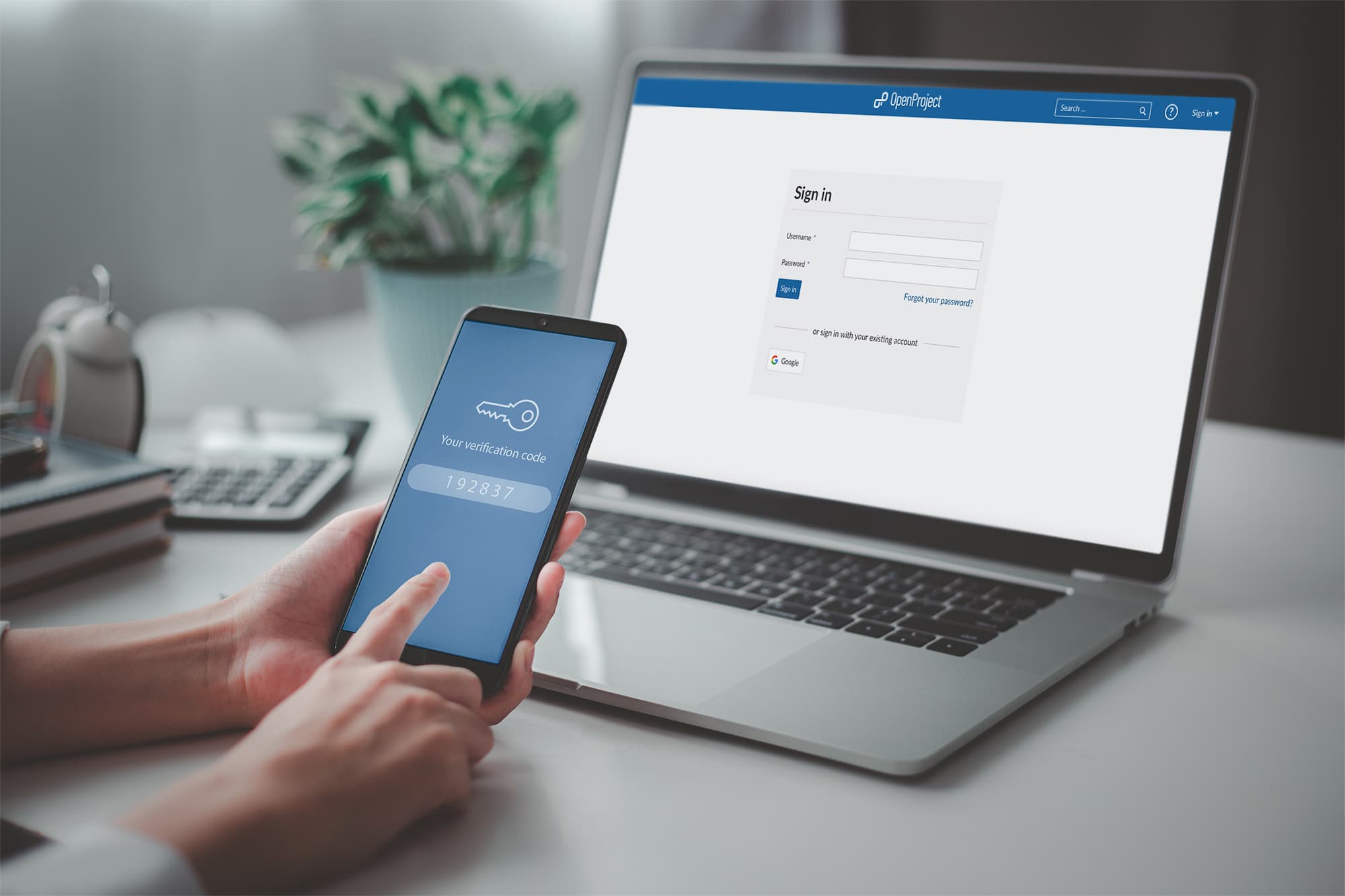
Authenticating something means proving it is real or genuine. This process is crucial for things like art, documents, and even online accounts. Authentication helps prevent fraud, ensures trust, and maintains the value of items or information. Imagine buying a rare painting only to find out it’s a fake. That’s where authentication steps in to save the day. From ancient artifacts to modern digital identities, the need for authenticating is everywhere. But how does it work? What methods are used? And why is it so important? Let’s dive into 33 fascinating facts about authenticating that will answer all your questions and more!
What is Authentication?
Authentication is the process of verifying the identity of a person or device. It's crucial for security in both physical and digital spaces. Here are some fascinating facts about authentication.
-
Passwords are the most common form of authentication. Despite their ubiquity, they are often the weakest link in security due to poor user practices like reusing passwords.
-
Multi-factor authentication (MFA) adds extra layers of security. MFA requires two or more verification methods, such as a password and a fingerprint, making unauthorized access much harder.
-
Biometric authentication uses unique physical traits. Fingerprints, facial recognition, and iris scans are examples. These methods are harder to fake compared to passwords.
-
Two-factor authentication (2FA) is a subset of MFA. It typically combines something you know (password) with something you have (smartphone).
-
Single sign-on (SSO) simplifies user access. SSO allows users to log in once and gain access to multiple systems without re-entering credentials.
Historical Background of Authentication
Understanding the history of authentication helps us appreciate its evolution and importance.
-
Passwords date back to ancient times. Roman soldiers used passwords to identify friend from foe.
-
The first computer password was created in the 1960s. MIT's Compatible Time-Sharing System (CTSS) used passwords to secure user accounts.
-
Biometric authentication has roots in the 19th century. Fingerprint analysis was first used for criminal identification in the 1800s.
-
The concept of two-factor authentication emerged in the 1980s. Early implementations used hardware tokens to generate one-time passwords.
-
Public key infrastructure (PKI) was developed in the 1970s. PKI uses cryptographic keys to secure communications and authenticate users.
Modern Authentication Methods
Today's technology offers a variety of sophisticated authentication methods.
-
Smart cards are widely used in corporate environments. These cards store cryptographic keys and require a PIN for access.
-
Voice recognition is gaining popularity. This method analyzes vocal characteristics to verify identity.
-
Behavioral biometrics track user habits. Typing patterns, mouse movements, and even walking gait can be used for authentication.
-
Token-based authentication uses physical devices. USB tokens and smart cards are common examples.
-
OAuth is a protocol for token-based authentication. It allows third-party services to exchange user information securely.
Authentication in Everyday Life
Authentication isn't just for tech geeks; it's part of daily life.
-
ATMs use PINs for authentication. This simple method has been in use since the 1960s.
-
Smartphones often use biometric authentication. Fingerprint and facial recognition are standard features on many devices.
-
Online banking relies heavily on 2FA. Banks often require a password and a code sent to your phone.
-
Social media platforms offer 2FA options. This adds an extra layer of security to your accounts.
-
E-commerce sites use various authentication methods. Credit card verification codes and 3D Secure are common.
Challenges in Authentication
Despite advancements, authentication faces several challenges.
-
Phishing attacks target authentication methods. Cybercriminals trick users into revealing their credentials.
-
Password fatigue is a real issue. Users struggle to remember multiple complex passwords.
-
Biometric data can be stolen. Hackers have found ways to replicate fingerprints and facial features.
-
Man-in-the-middle attacks intercept authentication data. These attacks can compromise even secure connections.
-
Social engineering exploits human psychology. Attackers manipulate people into divulging confidential information.
Future of Authentication
The future holds exciting possibilities for authentication technologies.
-
Quantum cryptography promises unbreakable security. It uses the principles of quantum mechanics to secure data.
-
Blockchain technology can enhance authentication. Decentralized ledgers provide a tamper-proof way to verify identities.
-
Artificial intelligence (AI) improves behavioral biometrics. AI can analyze vast amounts of data to detect anomalies.
-
Wearable devices may become authentication tools. Smartwatches and fitness trackers could verify identity based on health data.
-
Zero-trust security models are gaining traction. These models assume no one is trustworthy by default, requiring continuous verification.
Fun Facts about Authentication
Let's end with some lighter, yet intriguing, facts.
-
The longest password ever used was 1,273 characters long. It was created as a security experiment.
-
The most common password is still "123456." Despite warnings, many people use easily guessable passwords.
-
Some animals have unique biometric traits. For example, koalas have fingerprints almost identical to humans.
Final Thoughts on Authenticating
Authenticating is more than just verifying identity. It's about ensuring security, trust, and peace of mind. From passwords to biometrics, each method has its strengths and weaknesses. Understanding these can help you choose the best option for your needs. Remember, multi-factor authentication adds an extra layer of security, making it harder for unauthorized access. As technology evolves, so do the methods of authenticating. Staying informed about the latest trends and updates can keep you ahead of potential threats. Whether you're protecting personal information or securing business data, robust authentication practices are essential. Don't underestimate the power of a strong, unique password or the convenience of biometric verification. By prioritizing authentication, you're taking a crucial step in safeguarding your digital life. Stay vigilant, stay secure, and keep your information protected.
Was this page helpful?
Our commitment to delivering trustworthy and engaging content is at the heart of what we do. Each fact on our site is contributed by real users like you, bringing a wealth of diverse insights and information. To ensure the highest standards of accuracy and reliability, our dedicated editors meticulously review each submission. This process guarantees that the facts we share are not only fascinating but also credible. Trust in our commitment to quality and authenticity as you explore and learn with us.
